Prerequisite: Your team's Super Admin must initiate the Compliance Suite setup.
This guide will explain how to set up the Compliance Suite from the perspective of a designated compliance officer/user.
In order to start these steps you will need:
1) The activation token sent to you by your HighSide team Super Admin
2) To install HighSide on a new device that has no other instances of HighSide already running on it
Once you have received the activation token from your team's Super Admin you are ready to start.
Setup: Begin by opening up your new install of HighSide and select the "Sign In/Accept Invite" option. Next, you click, "Accept Email/SMS Invite" and input the compliance suite activation token you received from your Super Admin into the "Signup Token" field. (Much like accepting an invite as a regular HighSide user.)
Keys will be generated and a HighSide address will appear on your screen - you will need to copy this and send it to your team Super Admin in order for them to finish setting up the compliance suite. You will be stuck on this setup screen until they finish setup on their end.
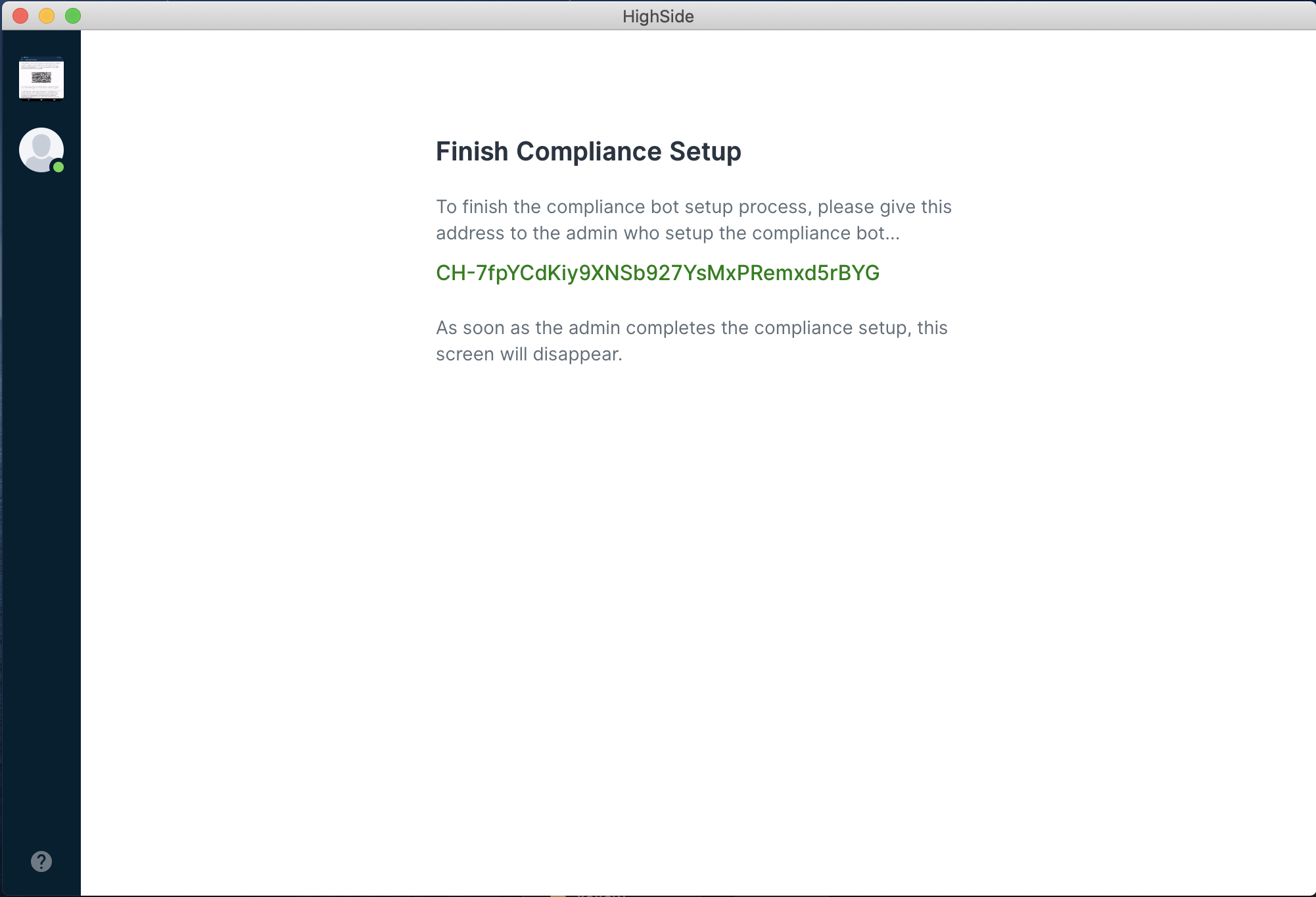
That's it! Once they complete the set up process on their end you will have full access to HighSide's Compliance Suite!
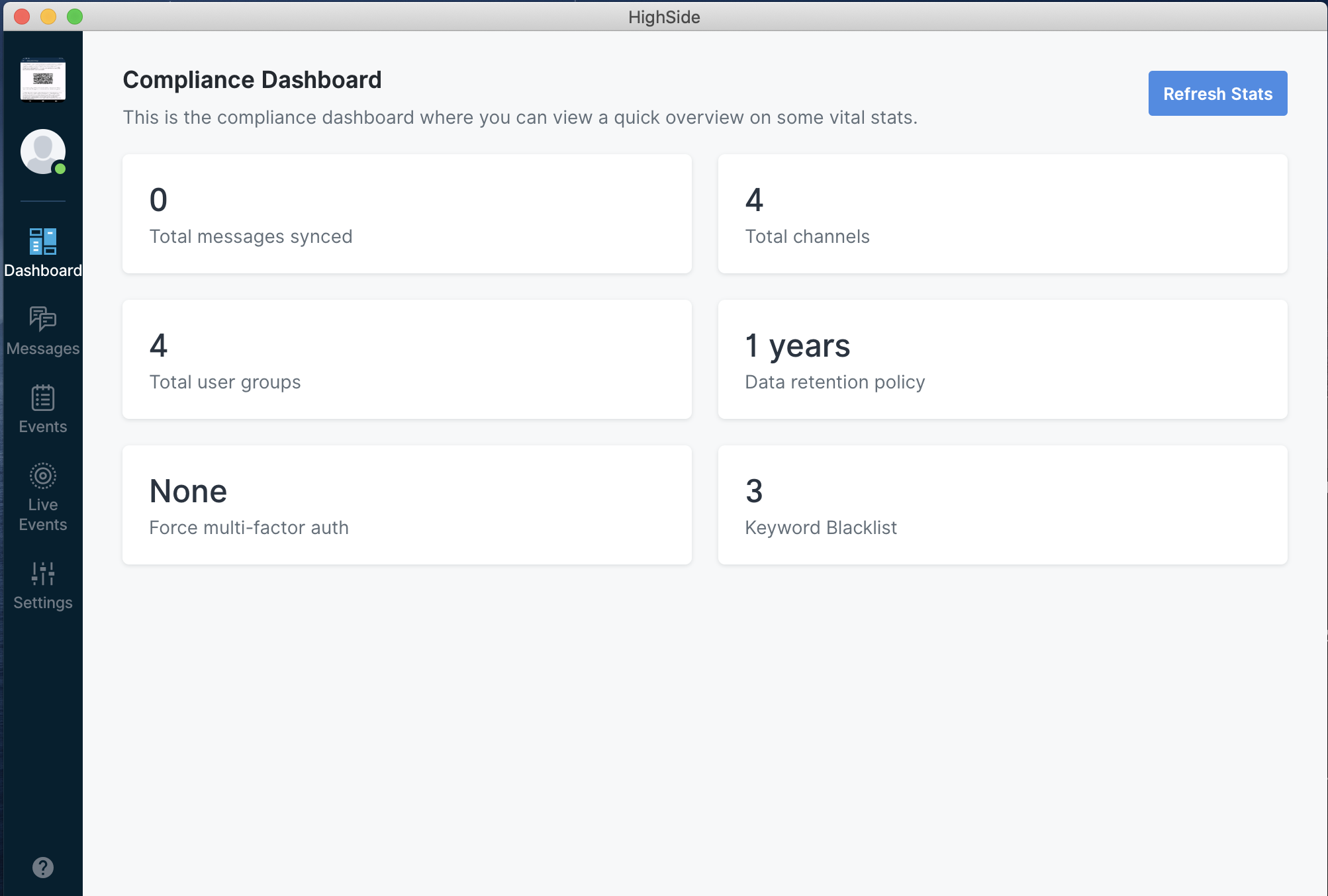
Hardware Requirements
The compliance suite can run on any desktop/laptop/server of your choosing, as long as it is capable of installing and running the latest version of the HighSide desktop client.
Hardware requirements are roughly proportional to the size of your team, or to the amount of data that is being transmitted team-wide. This is because the compliance suite maintains copies of all the events and data created by your team.
We recommend minimum hardware requirements of 1 gigahertz (GHz) or faster processor, 8GB of RAM or more, and a large hard drive.
For best performance/usability, a fast multi-core processor and as much RAM as possible is recommended.
Note that the compliance suite does not store local copies of attachments/NGR files, but the compliance user can download any file at any time on demand.
If you have any questions or concerns, please feel free to contact us for hardware/system recommendations.
Operations & Data Capture
Once successfully activated, the compliance suite will begin capturing and recording all events, messages and files shared by your team. Because of the way the keys/encryption work, it cannot retroactively capture data from points in time before it was activated. This means the compliance suite will not have access to messages/files or events from before the data of activation.
If the bot is deactivated by a team Super Admin, the compliance suite will not have access to any data transmitted during the deactivated state.
You do not need to keep the compliance suite itself open and running 24/7 in order for it to capture data - if the compliance suite loses internet connectivity or is is turned off, the next time the compliance suite reconnects, it will begin syncing all of your team's data from the last point in time it was connected.
Security Best Practices & Considerations
Because the compliance suite has access to all of your team's messages, files and logs, we highly recommend that you follow security best practices while setting up the compliance suite, installing it on a new device, and while operating the compliance suite.
The compliance suite can run on any desktop/laptop/server of your choosing, but we recommend that whatever device you choose be designated exclusively for running and operating the compliance suite.
What does this mean? If you choose to install the compliance suite on Desktop A, Desktop A should be purpose-built and used exclusively for running the compliance suite. Desktop A should not be used as a normal workstation; it should not be used to surf the internet, to run other apps or programs, to check email, etc. Desktop A should be exclusively used for the compliance suite.
Ideally, Desktop A would never connect to the internet for any purpose other than operating the compliance suite. It would be stored in a secure location and accessed only by approved compliance users. It should never be connected to a printer or external media device like a USB.
Why? Because every time you surf the internet, install an app, open an email or click on a link, you can potentially compromise the security of Desktop A (even if it is running antivirus software). Desktop A could become infected with malware, or the keys for the compliance suite could become compromised. For these reasons, it is advisable to control access to, and limit use of, Desktop A.
The designated compliance user should always be using multiple forms of MFA for their account. Additionally, the desktop/server/laptop that is running the compliance suite should have strong OS-level disk encryption (popular operating systems such as Mac OS and Windows 10 offer this by default).
Please keep the device's operating system fully patched and up to date.
For questions or assistance in securing/selecting a device for the compliance suite, please contact us.
